New Era of Caller Identification – Calling Name Presentation (CNAP)

The Telecom Regulatory Authority of India is soon going to introduce the Calling Name Presentation (CNAP) system in India. With the implementation of CNAP, Indians may be able to see the verified name of the caller along with a number while picking up calls. India is planning to regulate calls and messages to help reduce […]
Explore the Hidden Security Powerhouse of Google

When it comes to internet security, many people do not know the strongest protection available today. It’s already in your Gmail account. Not only Google offers free email, it also offers you a personal cyber security suite that is packed with layers of protection, privacy, and peace of mind. Here’s a guide to the most […]
The Social Media Influencer Vigilantes : Between Heroism and Hubris

In the massive digital landscape of India, where over 800 million people have access to the internet, a new breed of internet personalities has emerged, Social Media Influencer Vigilantes. At first glance, Social Media Influencers appear as heroes / social activists, who are actually ordinary citizens exposing scams, fighting unethical business practices, calling out corrupt […]
Race for Views and Money – Where Filth and Hatred is the New Norm

Content creation should about telling stories, being creative, and having real talent. The loudest, most bizarre voices receive the most attention in today’s rat race for views. From gaming and entertainment to political discourse, a large number of influencers are normalising hate speech, vulgarity, and false narratives to increase views, likes, and brand partnerships. Nowadays, […]
Jump Deposit Scam : UPI Based Fraud

The world has become interconnected and banking transactions have become a great convenience. However, this also opened up opportunity for fraudsters to take advantage of innocent individuals and businesses. Jump Deposit Scam is one such scheme which is based on deception which preys on trust and urgency to manipulate victims to loose their money. Modus […]
Beware of Fake Extortion Calls: A Guide to Staying Safe

As the world rapidly becomes interconnected, the menace of extortion calls in the name of government departments has grown exponentially with swindlers using technology to impersonate police officers, lawyers, Department of Telecommunications (DOT) officials, Telecom Regulatory Authority of India (TRAI) personnel, and even bank representatives. Most of these scams originate from abroad and prey upon […]
Quishing Attack

Along with the improvement in technology, the trends exhibited by cyber attackers also grow. Quishing is one of such emerging threats, a kind of phishing that primarily exploits a QR code to cheat an individual. Quishing makes use of QR codes unlike other types of phishing, which depend upon malicious links or email attachments. It […]
Unnecessary Access Requests in Mobile Apps
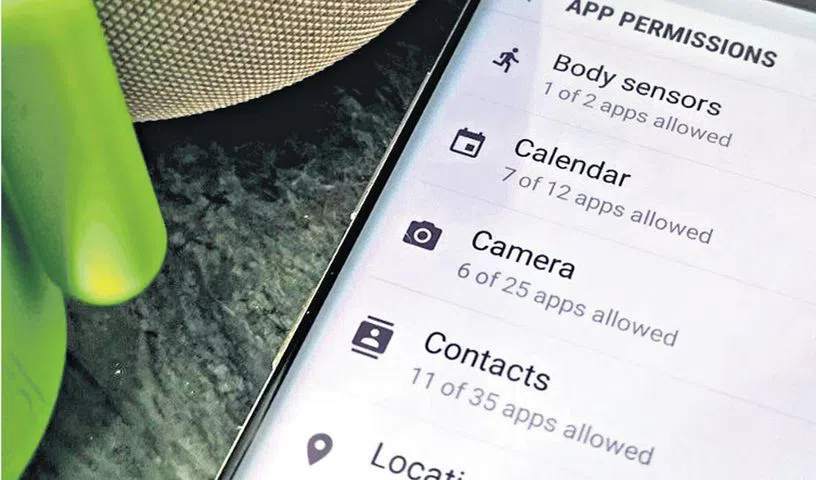
In an increasingly online culture, mobile applications have become a major part of our daily routine, providing a variety of Applications covering everything from communication and entertainment to productivity and money. However, the ease of use and utility given by these applications usually come at the risk of a Potential Breach of our personal data […]
All about Data Scrapping
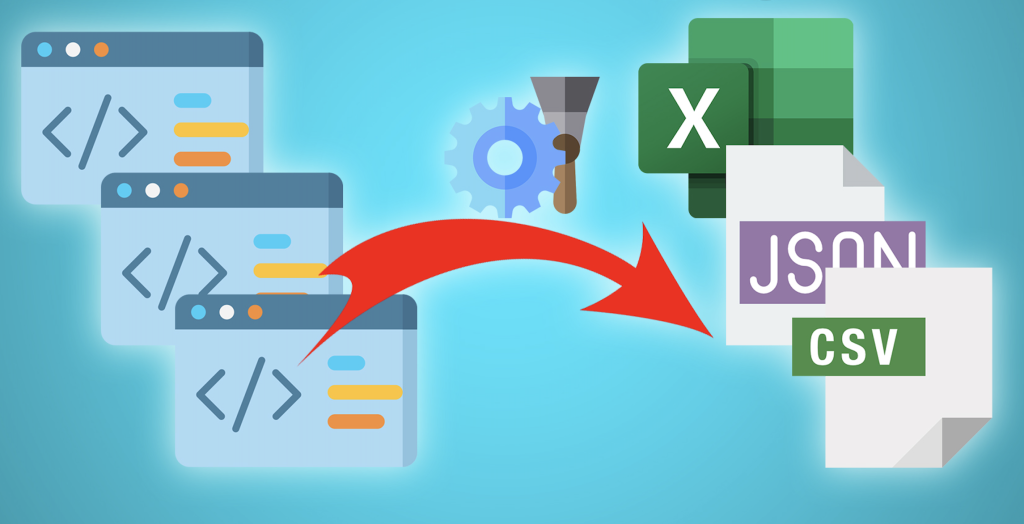
Data scraping, also referred to as web scraping or data extraction, refers to the automated process of extracting data from websites or online sources. By exploiting software tools and scripts, data scraping enables access to web pages, retrieval of required information, and saving it in a structured format for further analysis.The purpose of data scraping […]
Digital Wellbeing for Generation Z

Digital well-being refers to the state of positive physical, mental, ethical, and emotional health that individuals experience in their digital lives. It involves using digital technologies and online platforms in a balanced, safe, and responsible manner. a) Access to Information – Digital Wellbeing ensures that they can navigate this digital landscape effectively, discern reliable information […]


