In an increasingly online culture, mobile applications have become a major part of our daily routine, providing a variety of Applications covering everything from communication and entertainment to productivity and money. However, the ease of use and utility given by these applications usually come at the risk of a Potential Breach of our personal data and privacy. One common issue of concern is that specific applications ask for unauthorised access, which can lead to unlawful activities.
When installing apps, users should exercise caution by carefully evaluating the permissions necessary and considering whether they are consistent with the app’s functionality. Developers, too, play a vital role in ensuring that their programmes request just the necessary permissions and are transparent about how they use data.
Cybercrimes due to unnecessary access:
- Apps with excessive permissions can collect sensitive personal information without the user’s knowledge or consent (i.e., personal details, contact lists, location data, and saved passwords)
- Some apps might use unnecessary access to deliver malware or viruses to the user’s device through which cybercriminals can gain control over the device, steal data, monitor activities, or even launch more sophisticated attacks.
- Cybercriminals can then use this stolen data to conduct fraudulent transactions, drain bank accounts, or make unauthorised purchases.
- Apps requesting unnecessary permissions could use this access to create convincing phishing attacks. They will impersonate trusted entities and send targeted phishing emails, messages, or calls, leading users to reveal more personal information or financial credentials.
- Ransomware is installed on the user’s device unknowingly. Ransomware encrypts the user’s data and demands payment in exchange for the decryption key. Victims might lose access to their important files and data until they pay the ransoms.
- Some apps misuse by sending targeted advertisement, users are bombarded with invasive ads, or their online activities being tracked without their knowledge.
- Apps with unnecessary access to location services can track the user’s movements, leading to privacy breaches and potentially enabling stalking or targeted crimes.
- Excessive permissions can enable applications to generate fraudulent ad clicks or manipulate user data for advertising purposes.
- Some apps might use permissions to access microphones or cameras, enabling them to eavesdrop on conversations or spy on users without their knowledge
- Apps that request access to social media accounts or email addresses can potentially compromise these accounts, leading to unauthorised posts, messages, or even hijacking of the accounts.
Common Tips for Mobile Users:
- Rise in cyber-crimes requires stronger security with Two Factor Authentication (2FA). 2FA shall prevent all unauthorised accesses to your account. (i.e., SMS or Hardware Token or Push Notification)
- Set a strong passcode (i.e., Numerical or Pattern) and it’s important to consider disabling fingerprint or face login.
- Stick to downloading apps exclusively from the official Apple App Store, as Apple’s review process helps filter out malicious apps.
- Check how you Smartphone applications access your data – https://reports.exodus-privacy.eu.org/en/
- Disable lock screen notifications on your smartphone, it helps you keep your privacy by not letting others know your communications.
- Avoid Free Public and Wi-Fi hotspots as they are more desirable for hackers as it requires no authentication to establish a network connection.
- Download applications from official app stores like Google Play Store or Apple App Store. Avoid third-party app stores or downloading APK / DMZ files from unknown sources to reduce the risk of malware.
- Use VPN on your phones, it keeps all data that you send and receive on your phone encrypted, private, and secure.
- Enable Remote Wipe Capabilities just in case your phone is lost or stolen, having the ability to remotely wipe your data can protect your information from unauthorised access by fraudsters.
- Keep an eye on your data usage to spot any unusual activity that might indicate a security issue.
- Use Privacy Conscious Browsers as TOR, Brave or Duck Duck Go, just in case you don’t have the luxury to subscribe for VPN Software. Alternatively use all other browses in incognito mode.
- Fact-checking an image (Reverse image check) – https://images.google.com
- Un-shorten short web links – https://www.unshorten.it
- Allowing subscribers to telecom confirm their registered numbers and remove numbers that were registered without their knowledge. https://tafcop.dgtelecom.gov.in
- Allowing subscribers to identify the sender of bulk SMS. https://smsheader.trai.gov.in/
- Platform for determining whether the video was genuine or a deepfake. https://platform.sensity.ai/deepfake-detection
- Use end-to-end encryption messenger apps only.
Tips for Android Users:
- Setting up Screen lock for Android: Settings > Security > Screen Lock. (With Face ID or Touch ID or Passcode or Pattern)
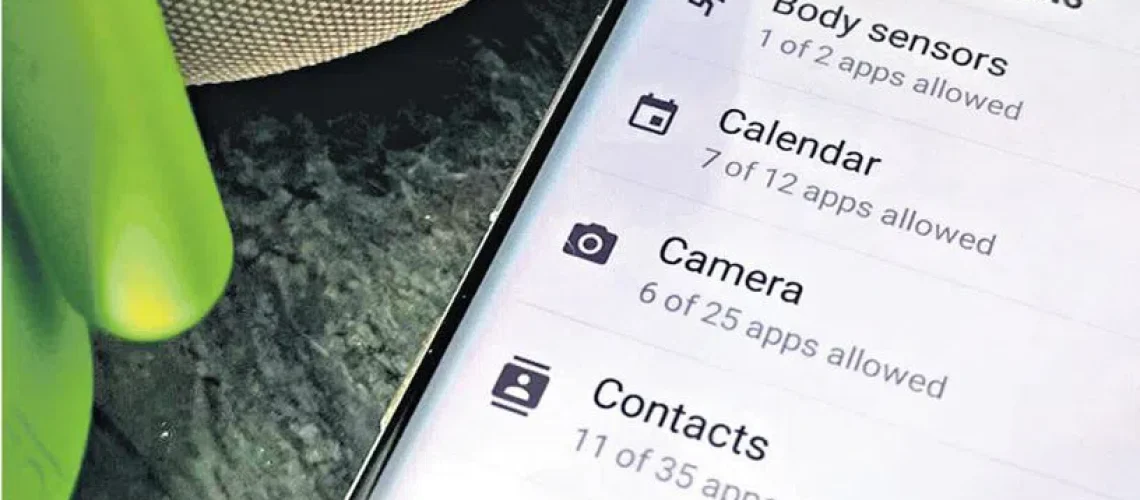
- Setting App Permissions on your Android phone. Settings Settings > Privacy > Permission Manage
- Enable Auto updates on your Android phone. Settings > General > Software Update.
- Enable Find My Device in android. Settings > Find My Device
- Keep sensitive notifications off the lock screen in android. Settings > General> Apps & notifications> Notifications > Lock screen. (You can be generic for all apps or set separately for each app).
- Disable Personalised Advertisements on your Android phone . Settings > Privacy > Ads
- Give your google account a privacy check. https://myaccount.google.com/privacycheckup
- Quickly block access for camera in Android. Settings> Security & privacy (Turn off Camera access or Microphone access).
- Keep an eye on the clipboard access. Settings> Privacy
Tips For iOS Users:
- Setting up Screen lock for iOS: Settings > Face ID & Passcode (With Face ID or Touch ID or Passcode or Pattern)
- Setting App Permissions on your iOS. Settings > Privacy & Security, then tap App Privacy Report. Grants access to (a) Location (b) Contacts (c) Microphone and (d) Camera.
- Enable Auto updates on your iOS phone. Settings > General > Software Update
- Enable Find My Device in iOS. Settings > Apple ID, iCloud, media & Purchases> Find My
- Keep sensitive notifications off the lock screen in iOS. Settings> Notifications (You can be generic for all apps or set separately for each app).
- Disable Personalised Advertisements on your iOS phone. Settings > Privacy & Security* > Apple Advertising
- Give your Apple account a privacy check. https://support.apple.com/en-gb/HT204145
- Quickly block access for camera in iOS. Go to Settings > Screen Time> Content & Privacy Restrictions (Turn off Camera access or Microphone access).