Unnecessary Access Requests in Mobile Apps
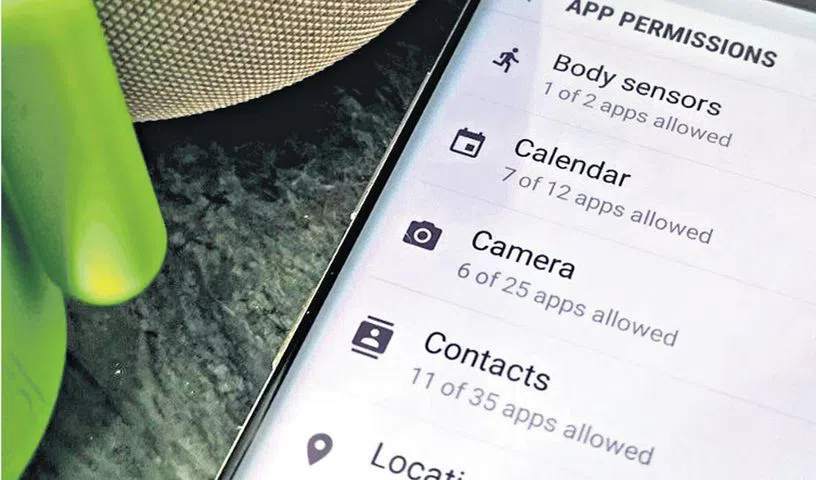
In an increasingly online culture, mobile applications have become a major part of our daily routine, providing a variety of Applications covering everything from communication and entertainment to productivity and money. However, the ease of use and utility given by these applications usually come at the risk of a Potential Breach of our personal data […]
All about Data Scrapping
Data scraping, also referred to as web scraping or data extraction, refers to the automated process of extracting data from websites or online sources. By exploiting software tools and scripts, data scraping enables access to web pages, retrieval of required information, and saving it in a structured format for further analysis.The purpose of data scraping […]
Digital Wellbeing for Generation Z

Digital well-being refers to the state of positive physical, mental, ethical, and emotional health that individuals experience in their digital lives. It involves using digital technologies and online platforms in a balanced, safe, and responsible manner. a) Access to Information – Digital Wellbeing ensures that they can navigate this digital landscape effectively, discern reliable information […]
Various Portals for Cyber Crime Reporting
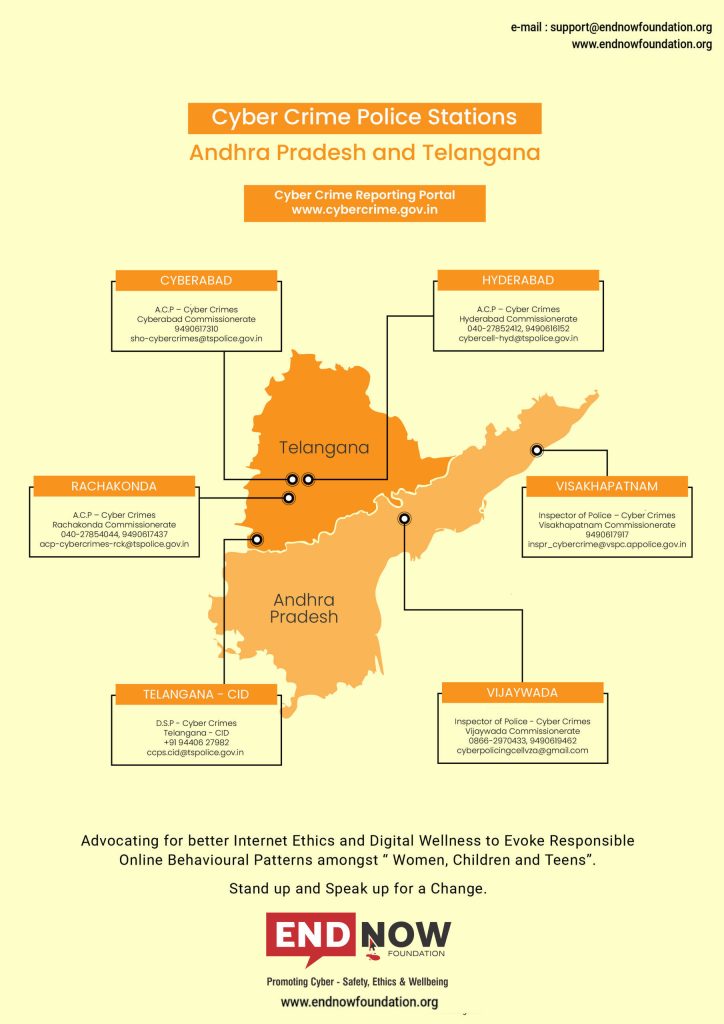
Reporting cybercrime in India involves following certain procedures to ensure that the authorities are made aware of the incident and can take appropriate action. Here are the steps you can take to report cybercrime in India: Collect as much evidence as possible related to the cybercrime. This shall include screenshots, emails, chat logs, bank transaction […]
All About Paid Blue Ticks & Verification Badges

The blue tick verification badge has traditionally been associated with authenticity and official recognition on the platform. However, with the introduction of a paid subscription model, there is a possibility that scammers or impersonators could exploit this system to deceive others. The decision by Twitter to offer blue-tick verification for a subscription fee has raised […]
Digital Wellbeing Approach to Employees

Digital wellbeing for employees refers to the practise of promoting a healthy and balanced relationship between employees and their digital devices and technology tools. It focuses on creating a work environment that supports employees’ mental and physical health while using technology, rather than allowing digital tools to become a source of stress, distraction, or burnout. […]
Use social media to stay effectively

Social media can be a powerful tool for connecting with others, building your personal brand, and promoting your business or ideas. However, it’s important to use social media effectively to reap its benefits. Your online actions could seriously limit educational, personal, or professional prospects in the future, i.e., a) What we post on social media […]
Protecting your child from sexual abuse

CSAM stands for Child Sexual Abuse Material. It refers to any visual depiction, including images or videos, that depicts sexually explicit conduct involving a minor, which is defined as anyone under the age of 18. CSAM is also commonly referred to as child pornography, although the term “child pornography” is considered outdated and has been […]
Being a better Digital Journalist

Digital intelligence in the context of journalism refers to the ability of journalists and news organisations to effectively navigate and leverage digital technologies and platforms to gather, analyse, produce, and distribute news content. It involves utilising various digital tools, techniques, and strategies to enhance the overall journalistic process and adapt to the changing media landscape. […]
Safeguard your personal data

Data protection refers to the practices and technologies used to safeguard sensitive and personal information from unauthorised access, use, disclosure, modification, or destruction. It involves a range of measures, including technical, organisational, and legal steps, to ensure that data is kept safe and secure at all times. Our personal digital rights as per GPDR include […]


