Why do people Vent on Social-Media?

Venting on social media refers expressions of our emotions, frustrations, thoughts, or grievances openly and publicly on social media platforms. Sharing personal experiences, problems, or feelings with a wide audience, often with the intention of seeking , support, validation, or letting off anger or frustration over an issue with individual or an organisation. Venting mostly […]
Unnecessary Access Requests in Mobile Apps
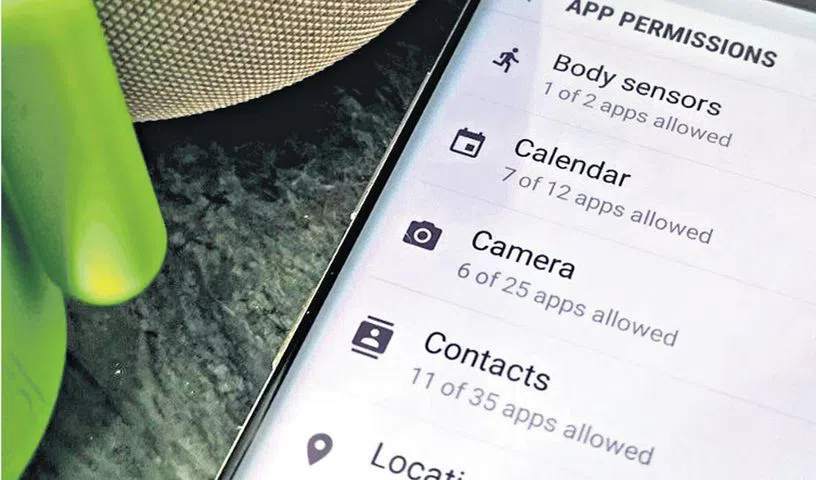
In an increasingly online culture, mobile applications have become a major part of our daily routine, providing a variety of Applications covering everything from communication and entertainment to productivity and money. However, the ease of use and utility given by these applications usually come at the risk of a Potential Breach of our personal data […]
Frauds galore in the name of Income Tax

Digital technology is currently advancing rapidly, and fraudsters are also looking to exploit it as much as possible, and now they are targeting innocent taxpayers. Fraudsters are using Social engineering tactics, which is the practise or art of convincing people to compromise their personal information. They are targeting members who have a PAN card and […]
Don’t take the AI Deep Fake Bait

Artificial Intelligence (AI) focuses on creating intelligent machines that can perform tasks that typically require human intelligence, such as understanding natural language, recognising images, making decisions, and solving complex problems. Few possible malicious and criminal use of Al-powered deepfakes (a) Harassing or humiliating an individual and destroying their image and credibility (b) Luring employees into […]
All about Data Scrapping
Data scraping, also referred to as web scraping or data extraction, refers to the automated process of extracting data from websites or online sources. By exploiting software tools and scripts, data scraping enables access to web pages, retrieval of required information, and saving it in a structured format for further analysis.The purpose of data scraping […]
Digital Wellbeing for Generation Z

Digital well-being refers to the state of positive physical, mental, ethical, and emotional health that individuals experience in their digital lives. It involves using digital technologies and online platforms in a balanced, safe, and responsible manner. a) Access to Information – Digital Wellbeing ensures that they can navigate this digital landscape effectively, discern reliable information […]
Various Portals for Cyber Crime Reporting
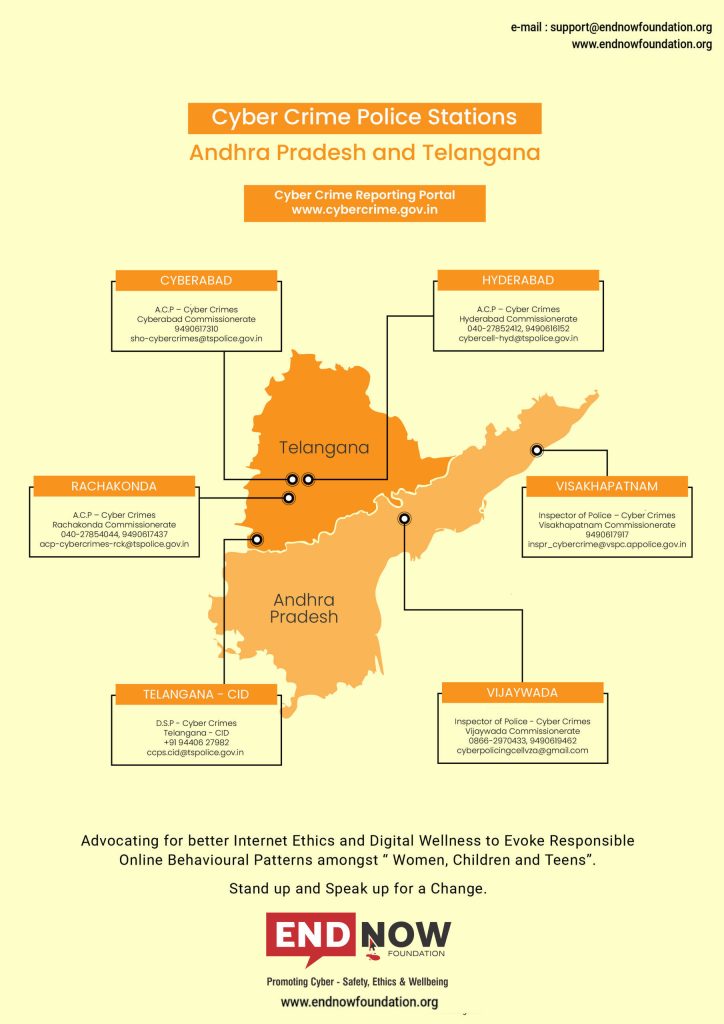
Reporting cybercrime in India involves following certain procedures to ensure that the authorities are made aware of the incident and can take appropriate action. Here are the steps you can take to report cybercrime in India: Collect as much evidence as possible related to the cybercrime. This shall include screenshots, emails, chat logs, bank transaction […]
All About Paid Blue Ticks & Verification Badges

The blue tick verification badge has traditionally been associated with authenticity and official recognition on the platform. However, with the introduction of a paid subscription model, there is a possibility that scammers or impersonators could exploit this system to deceive others. The decision by Twitter to offer blue-tick verification for a subscription fee has raised […]
Digital Wellbeing Approach to Employees

Digital wellbeing for employees refers to the practise of promoting a healthy and balanced relationship between employees and their digital devices and technology tools. It focuses on creating a work environment that supports employees’ mental and physical health while using technology, rather than allowing digital tools to become a source of stress, distraction, or burnout. […]
Use social media to stay effectively

Social media can be a powerful tool for connecting with others, building your personal brand, and promoting your business or ideas. However, it’s important to use social media effectively to reap its benefits. Your online actions could seriously limit educational, personal, or professional prospects in the future, i.e., a) What we post on social media […]


